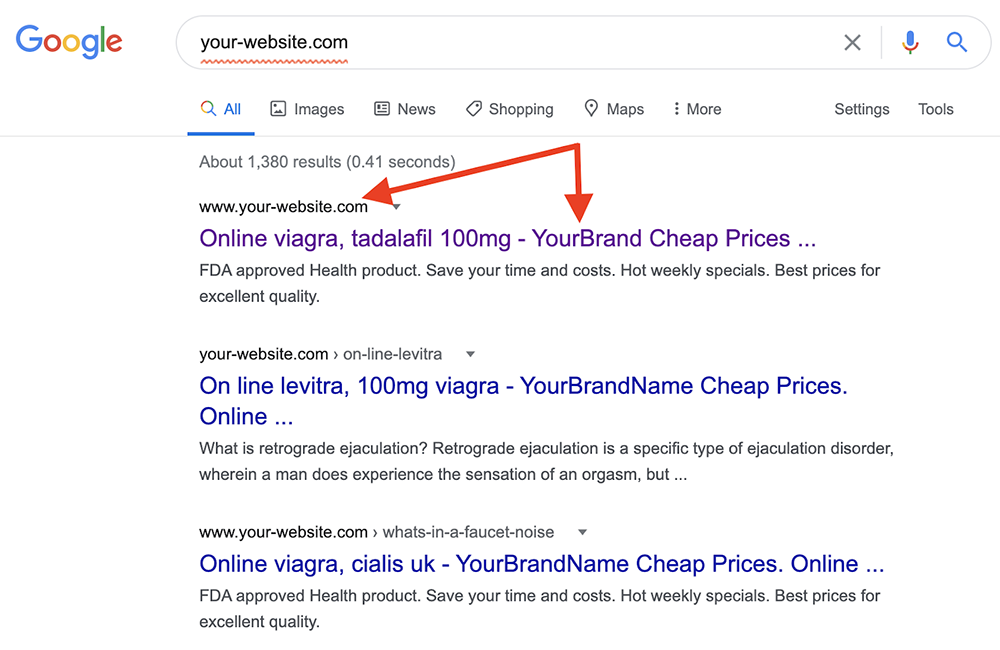
Did you search for your WordPress website on Google and found a bizarre pharma title appended to it in the search results? Yes? Then your WordPress website is a victim of the WordPress Pharma Hack!
Over 40% of all sites available on the Internet run on WordPress CMS. Its popularity has attracted many hackers and SEO spammers to earn profit from genuine and well-established websites that have good traffic and search engine presence.
Hackers use different malicious approaches to attack a WP site, leading to monetary and trust issues for your business and its growth. The results of such attacks can also lead to a sudden decrease in the number of website visitors, or the search engines displaying warnings before accessing your WordPress website.
How to Fix the WordPress Pharma Hack?
The best part for the hackers about this hack is that it is not easily discoverable and hence can stay on your website for a long time. There could be a chance that you do not see any symptoms of the WordPress pharma hack, but your site may be under the control of hackers.
You need to scan the code, figure out the vulnerabilities present on your WordPress site, and restore your website. Follow these steps to do it yourself:
Step 1: Create a Backup for Your Website
it’s good practice to take a backup of your current site. In the event of anything going wrong, you can restore this version. Make sure to take the backup file in a compressed format like a .zip file.
Step 2: Scan the Website for Malware
Scan your website for malware and malicious files. You can use the ‘wordfence plugin’ , or get expert malware cleanup.
Step 3: Remove the Infected Files
Navigate to the /wp-contents/ directory after connecting to your host server via FTP or file manager and look for hacked files or plugins. These files have words like .class, .cache, .old that look similar to plugin files.
The presence of dot (.) in front of the file name makes them hidden and are not visible till you select the ‘show hidden files’ option. Remove all such hidden files.
Step 4: Clear the Temp Directory
Hackers use the temp files and folder to avoid corruption during the malware implantation on your WordPress website. The /wp-contents/temp/ directory can generate temporary files for the WordPress pharma hack; it is advised to clear this folder in case you see suspicious entries.
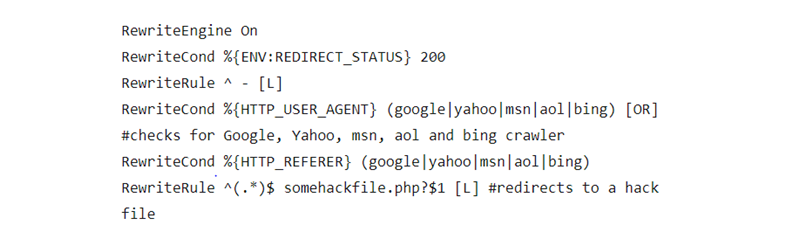
Step 5: Check the .htaccess File Content
The .htaccess file is a configuration file for the server that defines how server requests are processed. Attackers can use these files to hack into your website. Search for the code given below or regenerate a new .htaccess file from the WordPress dashboard.
Step 6: Removal Malicious Code from Your DB
Again, every time you work with your website’s database, it is mandatory to take a backup. Working with the database is a sensitive step, and a backup would help you to roll back the changes if something goes wrong.
For cleaning the database manually, follow these steps:
- Go to your phpMyAdmin panel
- Select the database
- Click on the wp_options table
- Search for the malicious entries that could be present in your database. Some of the common entries are:
- wp_check_hash
- Class_generic_ssupport
- widget_generic_support
- Ftp_credentials
- rss_%
Be cautious and do not delete any other important information from this table, as it could cause your site to crash.