How To Fix Japanese Keyword Hack
1. Backup your site before cleaning
It is always a good practice to create a complete backup of your WordPress website before fixing any bug or vulnerability in it. This makes it comfortable to undo the changes if something goes wrong while cleaning the website. This backup must have all the core files, plugin and theme files, and your website’s database.
2. Remove any newly created user accounts in the Search Console
Check “Users and Property Owners” tab – this is where you can find out if hackers have admin access to your site. If you don’t recognize any user or see suspicious activity, immediately revoke their access. Hackers add spammy Gmail accounts as admins so that they can change your site’s settings like sitemaps and geo-targeting.
3. Run a Malware Scan
Scan your website for malware and malicious files. You can use the ‘wordfence plugin’ , or get expert malware cleanup.
4. Check your .htaccess file
Hackers often use the .htaccess file to redirect users & search engines to malicious pages. Verify the contents of the .htaccess file from a last known clean version of your backups. If you find any suspicious code, comment it out by putting the ‘#’ character in front of the rule.
5. Copy your WordPress configuration database connection strings
Your wp-config file is your website’s configuration file and clearly most wanted by hackers. In case of a hack, the attacker can insert malicious content in this file too. Make sure to thoroughly scan this file and remove the unfamiliar contents to remove Japanese SEO spam from your website.
However, editing wp-config may create a mess if you unknowingly delete something vital. Thus, in spite of editing it, you can take a copy of your WordPress database connection strings and make a totally new file out of this. Then, delete the former infected wp-config file. A word of caution – wrongly editing the wp-config file can take your website down, so be very careful!
6. Check the recently modified files
You can find any recently modified files by following these steps:
– Log in to your web server via SSH.
– Execute the following command to find the most modified files
find /path-of-www -type f -printf '%TY-%Tm-%Td %TT %p\n' | sort -r
7. Replace the core files, plugin files & theme files
You can replace the infected core files with the original versions of the same from WordPress.org. After downloading the fresh and updated versions of these files & directories, you can delete the older ones.
8. Check your uploads directory
Check your wp-content/uploads directory for files with blacklisted extensions, like .php, .js and .ico. If you find such files, check the content for characters like base64_decode, rot13, eval, strrev, gzinflate, etc. Eliminate files all such files as they are can be malicious.
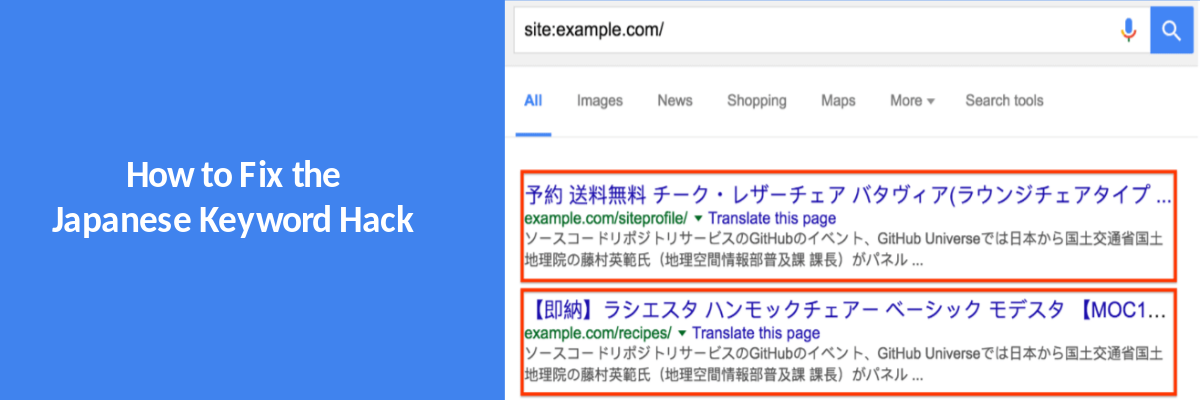
9. Check your sitemap
A hacker may have modified or added a new sitemap to index the Japanese SEO Spam pages quickly. If you notice any suspicious links in the sitemap, quickly update your CMS core files from a last known clean backup.